Written by Dr Gavriel (Gav) Schneider CCRO, CPP, FISRM, ChFInstP.
The need to protect and secure assets, information and people is not a new notion. However, the need to address fast evolving threats, targeting interdependent assets in a complex world, makes the challenge more difficult than ever. In his 2023 threat update briefing Mike Burgess, the Director General of Security (Australian Government ASIO) stated ”The security environment is complex, challenging and changing. ‘Complex’ because the threats are increasingly intersecting, emerging from new places and blurring traditional distinctions.“
Over the last two and half decades, I have operated in over 16 countries and worked with a very broad range of critical Infrastructure (CI) asset owners and system operators. These include Government’s, Energy, Finance, Education, Health, Water, Passenger transport and Aviation sectors to name a few. There are so many lessons learned through this experience that I often talk about at conferences, or in podcasts, but have not purposefully documented. My aim is to share some of these ‘lessons learned’ in this article.
As we move into an era of new security challenges, and a shift to a higher state of regulation and oversight for critical infrastructure in Australia as well as the application of the new protect duty legislation / Martyns’s Law3 in the UK, there are several key considerations that should be taken into account.
Whilst there are far too many to list in one article, here are my top 7.
Note: they are all important and not listed in in order of priority. In fact, they integrate and synergise to create a good outcome.
1 Overcome Ignorance, Negligence and Denial
Without an honest assessment of where you are, you cannot get to where you want to be.
Addressing risk in a balanced and appropriate manner requires a level of maturity and understanding about your own threat exposure, vulnerability, asset and supply chain criticality. It also requires a level of honesty and the right attitude. Over hundreds of project deliveries, we have found that there is an appropriate balance of external and internal resources required to get a great security and risk outcome. In order to get the most accurate picture of what is happening ‘in reality on the ground’ and in practice, independent audit and assurance is required. Whilst this is nothing new for the Financial services sector, who have long applied the three lines of defence model (3-LOD), it is something we have found to be missing in many other sectors.
Additionally, there is a requirement for an open and honest assessment of actual internal capability and capacity. Simply put, appointing one or two people to handle the full ambit of security and risk is highly unlikely to be very effective. We all have strengths and weaknesses, and assuming someone can be an expert in so many domains is a recipe for disaster. In fact, organisations are often setting their resources up for failure or mental health challenges (as we are now seeing in the cyber security fraternity4) with unrealistic expectations. Unrealistic expectations of delivery in high risk and regulated environments, with very limited budget or support, is like trying to stop a bush fire with a water pistol. The starting point of success in this space is the humility to admit that sometimes your organisation may actually need help, or that internal resources may not know it all. Importantly, the converse of this is also true, too many resources may be inefficient, expensive and/or not add the value required. It is crucially important that trust is placed in the right external partners, as they will have an intimate exposure to what you do and how you operate. If they do not have adequate experience and credentials, you may spend a lot of money with very little tangible risk reduction or increase in security posture.
Key takeaway: Cultivate situated humility, scope your needs honestly, and develop trusted partner relationships.
2 Risk and security management is a team-sport
You are only as strong as your weakest link.
The need to secure complex systems is not an easily tackled challenge. It requires an acceptance that both internal and external stakeholders need to collaborate, and that silos within organisations need to be overcome. This aspect is especially important when we consider managing aspects such as insider risk or supply chain risk, with many organisations today being reliant on exceptionally complicated and interwoven supply chains and outsourced work forces.
There are three main guiding points to be considered here:
- Integrating initiatives across internal silos; easily said but tough in practice.
- Work with supply chain providers to create an open and honest basis that is more than just terms in a contract. If your supply chain providers cannot be open and transparent about their own potential risk and challenges, then you are simply pretending/hoping things are ok.
- Don’t forget about the ‘Human’ in the system; we are transitioning out of era that was highly process and efficiency focused into a more human centric approach that balances the needs of our people with the operational efficiencies.
Key takeaway: Look at the whole system, bust silos and treat your people and contractors as though they are part of the solution.
3 Don’t fall into the trap of risk and security theatre
Wishing a risk away or pretending it’s been addressed is not risk management
There is a tendency based on human bias and aligned to ignorance, negligence and denial, to implement one or two tangible or tokenistic aspects and then consider the risk to have been addressed. The concept of security (risk) theatre5 which highlights this issue has so many relevant examples, but the following are a few common examples we have experienced:
-
- IT has installed a firewall and we have virus protection, so we don’t need to worry about Cyber Security.
-
- HR does background checks when we hire people, so we don’t need to worry about vetting.
-
- We have cameras, so we don’t need to look at security guards or vice versa.
-
- We have robust contracts in place with suppliers, so our supply chain security is not an issue as they need maintain a minimum standard as per the contract.
-
- It’s never happened before to us, so our security and risk management must be more than adequate.
There are many ways we can manage the limitations associated with a security and risk theatre mindset. Primarily mitigations hinge on culture and a requirement to develop a robust approach to the way we think about and manage risk. Cultivating an attitude of continuous improvement is crucial, as is a robust audit and assurance programs. Conducting regular tests and exercises to identify gaps in a system, as well as to improve the way we tackle risk, is also very important. Utilising experts not caught up in a ‘loop of denial’ can be very useful too – you just have to make sure your internal structures are open to the feedback, and that your organisation has a measured risk appetite and tolerance approach.
Key takeaway: Don’t fall into the trap of security and risk theatre, mange biases and seek assurance via testing and exercising.
4 Don’t fall into the Reactive spending cycle – get ahead of the curve
Short term savings may come at a significant cost.
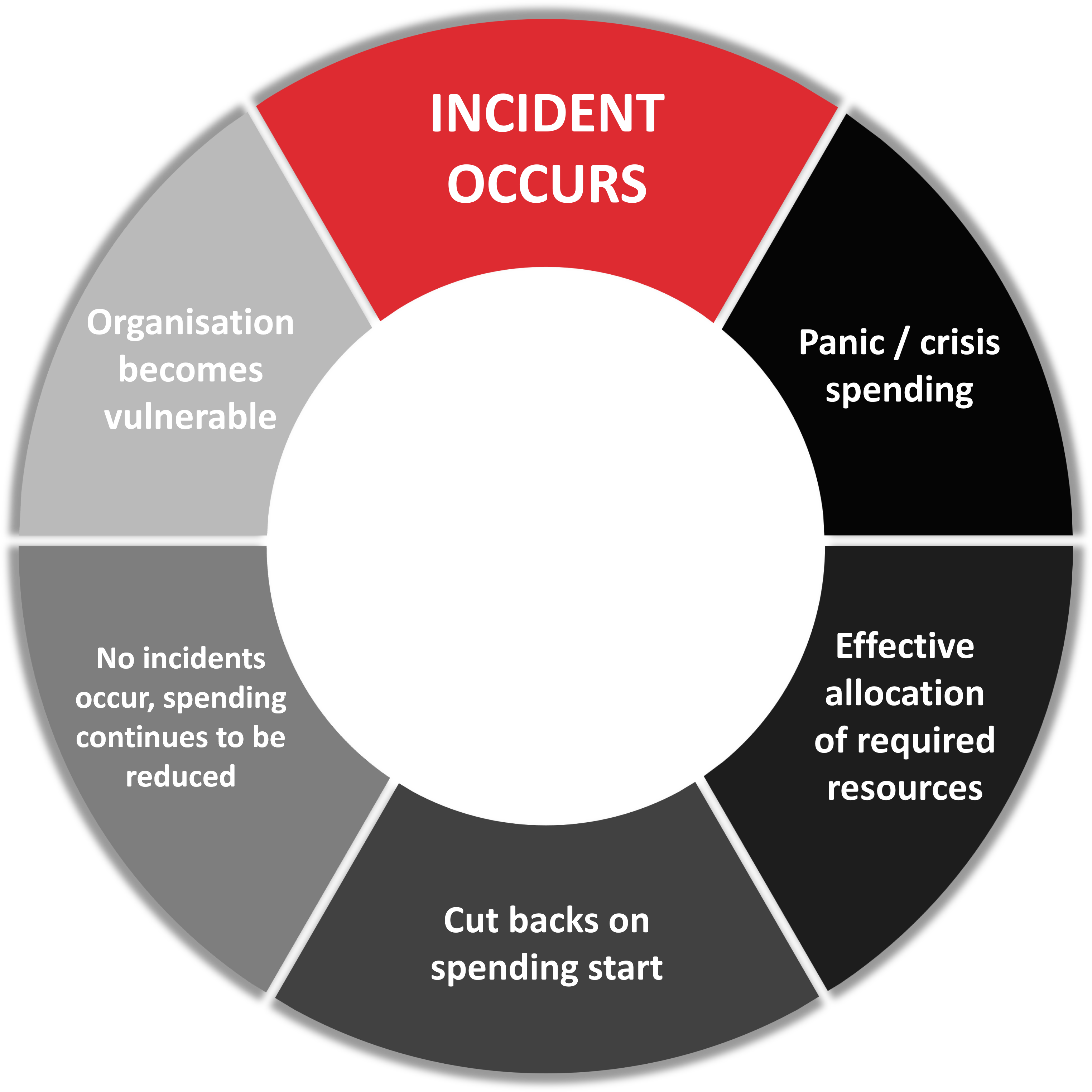
Almost ten years ago, Professor Anthony Minnaar and I penned an article describing the approach to reactive spending6 on security and risk as per the below diagram. Today, it seems more of an issue than ever. We need to be very careful how we make budget decisions as perceived short-term savings can really hurt when an incident occurs. Security risk is a very tough area to measure effective Return on Investment (ROI). It’s hard, because if security and risk experts perform their jobs properly, then ideally nothing bad happens. Short-term thinking and poor situational awareness often combined with a limited understanding of the threat and risk exposure means that, in many cases, the absence of clear and prevented attacks creates the perception that there is no need to maintain spending on security.
While it may be true that spend and activities should flex (scale up and scale down), based on threat and risk, some sectors (such as Critical Infrastructure), will always be attractive targets. As such, a longer-term spending cycle mindset has actually been shown to be cheaper in the long run than simply not spending and then having to spend a lot and allocate a disproportionate amount of resourcing when an incident occurs. Recent cyber-attacks have shown that the impact of an incident can, in some cases, be fatal for a business – or at least cost significantly more than a bit of proactive prevention. The old saying ‘an ounce of prevention is worth a ton of cure’, has never been more relevant.
On the flip side, it is also important not to be caught up in a cycle of overspending (which is actually closely linked to security theatre). There are always ways to improve security posture and readiness, even when there is no budget at all, as but one example – vigilance and mindset can be very effective if applied properly and may not cost much to develop and implement.
Key takeaway: The Reactive Risk Spending model – not a good way to budget.
5 Take the best out of Compliance, Resilience and Presilience®
Compliance based mindsets are not enough anymore.
Security and risk are full of jargon and buzz words that often mean extraordinarily little to stakeholders not in the know. The term ‘resilience’ has become widely used as it should since it is very important for risk management. In fact, risk and resilience are two intertwined concepts. By definition7, a risk is something that is not certain and may or may not happen. Resilience is what we need when risks are realised. When it comes to managing the security risks associated with CI, there are very few cases where risk can be totally eliminated. Rather, we land up with a suite of treatments and controls that reduce the risk exposure to a reasonably practicable level within tolerance and appetite. We often forget that there is still a residual risk that is left over, and that almost all controls are fallible – especially when we are facing motivated and sophisticated threat actors. This is where the concept of ‘Presilience®’ comes into play. The primary attributes of a Presilience® centric approach to risk (the next level of resilience) are focused on Proactive Prevention and Opportunity Centrism. However, we cannot focus on Proactive Prevention and Opportunity Centrism unless our fundamental compliance and resilience aspect have been addressed.
To get the best out of spend in the current threat environment, a balance which allocates resources across compliance, resilience and Presilience® is recommended. Once an organisational culture has been developed that finds the applicable balance for that organisation between the three aspects, efficiencies across silos, enhanced vulnerability management and many other benefits can manifest, including employee motivation, engagement and performance being dramatically improved.
Key takeaway: To get the best out of spend in the current threat environment, a balance which allocates resources across compliance, resilience and Presilience® is recommended.
6 Culture eats strategy for breakfast
If you don’t engage your people and build the right culture, you are diminishing efficacy of your controls.
As Drucker’s8 famous saying goes ‘Culture eats strategy for breakfast’, it’s not good enough to develop a robust risk management program (the strategy and action plan to manage risk) based on policy, frameworks and guidance alone. The ability to successfully implement and sustain practices is crucial. In fact, in many cases organisations can expose themselves to greater risk and liability by developing strategies, policies and plans, and then failing to implement them or implementing them poorly.
Time and effort spent on developing the right culture that balances engagement with controls, and ties them back to strategic objectives, cannot be over emphasized as a critical success factor for any effective risk management program. A culture of learning and fairness means that staff are more likely to report issues or suspicious activities, will accept and embrace changes that make them safer and enhance organisational resilience, and ultimately will enable the evolution as Presilience® based thinking as a default.
Key takeaway: Measuring, changing and sustaining cultural is neither simple nor easy, but for those organisations that don’t invest in these activities and simply think that process, compliance-based, technical solutions will be enough, will remain significantly more vulnerable than organisations that implement the same with a dedicated focus on people and culture.
7 Implement a continuous loop cycle / Learning cycle
Without adaption and innovation, vulnerability and the likelihood of negative outcomes is dramatically increased.
There are so many times where we have been asked to do an assessment or conduct an audit and find that historical recommendations from previous audits or assessments have not been actioned, or have simply been ignored. As an asset owner or operator, aligned to a risk based regulatory system (such as the SoCI Legislation implemented by the Home Affairs CISC in Australia), you can set your own appetites and tolerances, but you also own the risk of things going wrong. There is nothing wrong with a gap or deficiency being identified during an audit or assessment cycle. In fact, it’s a gift if it can be identified and rectified before a negative outcome manifests. What is a problem, is the failure to own and address such aspects. Remember, if your audits and/or assessments are always telling you what you want to hear, they are not doing their job and you are most likely in a highly vulnerable position.
Some examples of good application include:
-
- Effective collaboration with internal and external stakeholders.
-
- Working with regulators and seeing regulation as an opportunity to do what is needed.
-
- Staying humble and open to a fact changing threat environment.
-
- Remembering it’s a journey, and as soon as an organisation makes statement such as “we have it all sorted or we are the best and don’t need help” I have found they are most likely in a lot of trouble, or simply don’t know what to do, or have many blind spots, and as such are actually an easy target for threat actors.
Key takeaway: Embrace regulation, audit and assurance as opportunities to perform at the right level and continuously improve.
Putting it all together
Risk and reward are intertwined. You cannot operate a risk-free organisation and expect not to be disrupted. I have shared a few hard learned lessons and some observations of what works and what does not, but in reality it is important to remember that every organisation and context is a bit different and what works in one place may not work in another. By developing a default position that focuses on a balanced approach to address solutions in the people, process and technology domains, we can better manage security and risk. By being proactive and taking the best of compliance, resilience and Presilience®, we can create the right cultural environment for a highly engaged and secure workforce.
We need to manage our biases, leverage internal and external expertise, and apply a long term, integrated approach to CI security and risk management.
When we do so, managing security and risk can actually be an operational and performance enabler, and complying with regulations is simply an easy output of a great culture and a well-run risk management program.



